This document outlines the setup process for integrating SAML-based Okta with Abacus.AI for Single Sign-On (SSO). It also includes best practices, security requirements, and answers to commonly asked enterprise questions.
Okta can be used to integrate with Abacus.AI for Single Sign-On (SSO) using either OAuth or SAML. This document provides step-by-step instructions for SAML, along with details on security requirements and troubleshooting. The OAuth instructions can be found here.
- Log in to your Okta Admin Console.
- Go to Applications → Click Create App Integration.
- Select SAML 2.0 as the sign-in method.
- Click Next, give your application a name (e.g., Abacus.AI), and optionally upload a logo.
Pleasee confirm the Abacus.AI organization you want to sign into. We’ll need the subdomain of the org, and it’ll be difficult to change it once this is set up and running in prod.
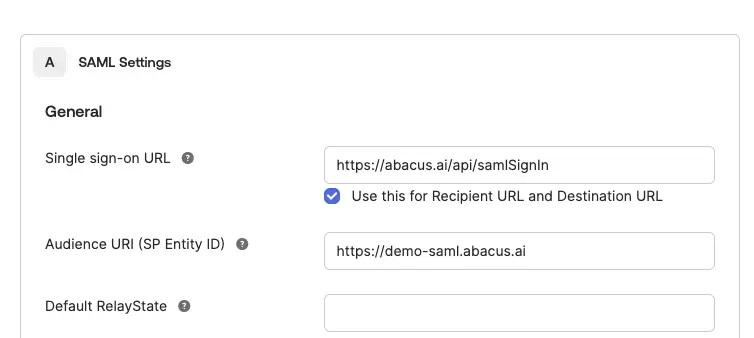
- Set the following configuration:
- Single Sign-On URL:
https://abacus.ai/api/samlSignIn
- Audience URI (SP Entity ID):
https://<subdomain>.abacus.ai
-
[Optional] Set "Default RelayState". By default we land user on https://.abacus.ai, which is the chat interface.
- If your use cases are not chat related, you may want to set this as https://abacus.ai/app/projects, which lands on the projects list page.
- Be careful that once you set an URI under https://abacus.ai/, we by default treat new users as platform user, who can have access to the projects and data.
We assume you will gate on who can be added as platform users to have more permissions.
-
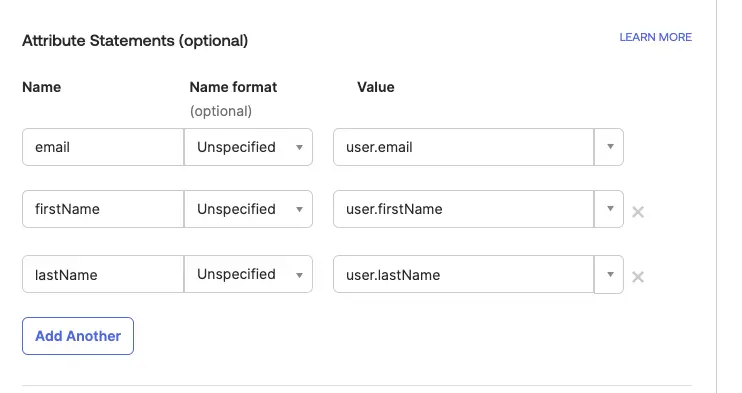
Under "Attribute Statements (claims)", set the following attributes:
email = user.email firstName = user.firstName lastName = user.lastName
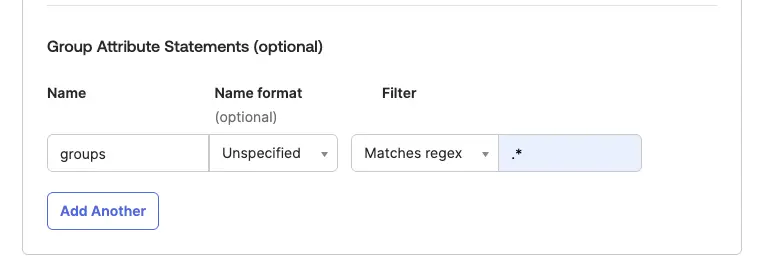
- [Optional] Set group attributes if needed:
- Use the name
groups.
- We suggest making group names descriptive and unique (e.g., include words/characters to identify the group is for your organization).
- Go to your application in the Okta Admin Console.
- Click on "Sign on" on the right of the General tab.
- Click "View SAML setup instructions on the right to access the metadata.
- Share the following information with Abacus.AI at
connectors@abacus.ai:
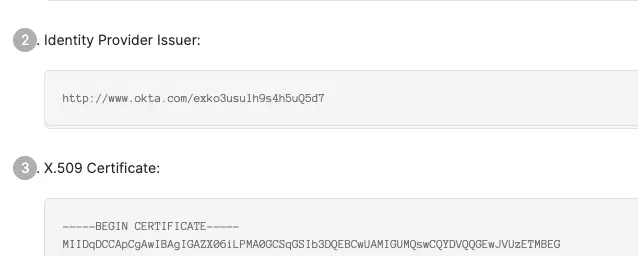
- Option 1: Provide the IdP metadata file (this contains all of the necessary information, including the x509 certificate and issuer URL).
- Option 2: If the IdP metadata is not availble, then please provide the following:
- Identity Provider Issuer URL
- X.509 certificate
- Audience URI (SP Entity ID): This is your Abacus.AI organization subdomain (e.g.,
https://<subdomain>.abacus.ai).
- Go to your application, click Sign on on the right of General, then click View SAML setup instructions.
- Test the integration by signing in with SAML.
- Signed Responses: Signed SAML responses are required. Unsigned responses will be rejected.
- Session Expiration: Sessions expire after 24 hours of inactivity.
- Re-authentication: Re-authentication is required after logout.
- JIT Provisioning: New users are auto-created in Abacus.AI on first login based on SAML assertion attributes.
-
Invalid Audience URI (Entity ID mismatch):
- Error: "Audience URI is invalid" or "Invalid recipient."
- Cause: The audience or Entity ID in your IdP is incorrect.
- Fix: Match exactly with https://<subdomain>.abacus.ai. Watch for typos or slashes.
-
Missing or Mismatched Attributes:
- Error: "Invalid login" or user isn’t created via JIT provisioning.
- Cause: Required attributes like email, firstName, or lastName are missing.
- Fix: Ensure these are mapped and correctly named in IdP settings.
-
Invalid or Expired x509 Certificate:
- Error: "Signature validation failed" or "Untrusted certificate."
- Cause: Expired or mismatched certificate.
- Fix: Renew the certificate and share the updated one with support.
Debugging Tip:
- Use browser extensions like SAML-tracer to inspect assertions, detect missing attributes, or identify signature
issues.
- Yes, we currently restrict it to your registered org’s domain in the Abacus.AI platform
- By default, the landing page is
https://<subdomain>.abacus.ai . If you need a different page, please contact us at support@abacus.ai.
- It’s in the URL to access the chat app interface for your organization. If you're unsure, please contact support.
- Yes. We recommend testing with a few users before rolling out org-wide.
- Update the certificate in your IdP (Okta) and send the new x.509 cert to us at
connectors@abacus.ai.
- Remove the SAML application from your IdP or disconnect from your Abacus.AI organization settings. Reach out to
support if you need assistance.
- Admins can access authentication logs from your identity provider's dashboard (e.g., Okta) to review user
sign-ins, failures, and SAML assertions. For any issues traced back to Abacus.AI, please contact our support team.




